Software
Apple has mistakenly allowed a commonly deployed malware to run on Macs.

Apple has some of the strictest laws to discourage malicious apps from appearing in its app store, even though a bad app occasionally falls through the net. Last year, Apple took the hardest step yet by forcing developers to apply their security applications to run on millions of Macs unhindered.
The method that Apple calls "notarization" searches an app for security problems and malicious content. If accepted, Gatekeeper, the built-in Mac security scanning program, allows the app to run. Applications that do not pass the safety sniff test are refused, and are blocked from running.
But security experts claim they discovered the first Mac malware unintentionally notarized by Apple.
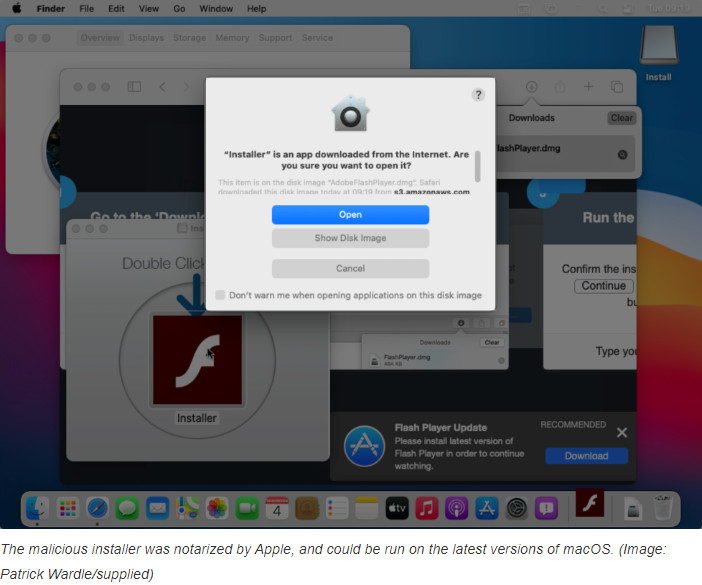
Peter Dantini, working with Patrick Wardle, a well-known Mac security researcher, has discovered a ransomware program disguised as an Adobe Flash installer. These campaigns are popular and have been running for years — even though Flash is scarcely used these days — and most run unrecognized code that Macs block directly after it is opened.
But Dantini and Wardle found that one malicious Flash installer had code notarized by Apple and was running on Macs.
Wardle reported that Apple had accepted the code used by famous Shlayer malware, which security firm Kaspersky claimed was the "most dangerous threat" Macs faced in 2019.
Shlayer is a type of adware that intercepts encrypted web traffic — including from HTTPS-enabled sites — and replaces websites and search results with its own ads, making fake ad money for operators.
This is the first thing I learned, Wardle wrote in a blog post, shared with TechCrunch.
Wardle said that means that Apple did not find the malicious code when it was sent and accepted to run on Macs — even on the unreleased beta edition of MacOS Big Sur, due later this year.
Since Wardle reached out, Apple deleted the notarized payloads, stopping the ransomware from operating on Macs in the future.
In a quote, Apple spokesperson said to TechCrunch, Malicious software is continually evolving, and Apple's notarization scheme lets us keep malware off the Mac and allows us to act quickly when it's detected. Upon discovering this adware, we revoked the detected version, disabled the developer account, and revoked the corresponding certificates. We thank the researchers for their support in keeping our users secure.
But Wardle said the attackers were back shortly after, with a new, notarized package, capable of circumventing Mac security all over again. Apple also stated that TechCrunch has already blocked the package. The game of the cat and the mouse begins.
